08. Monitoring Network Traffic
Monitoring Network Traffic Heading
Monitoring Network Traffic
ND545 C02 L03 A10 Monitoring Network Traffic Part 1 V2
Monitoring Network Traffic Notes
Recap:
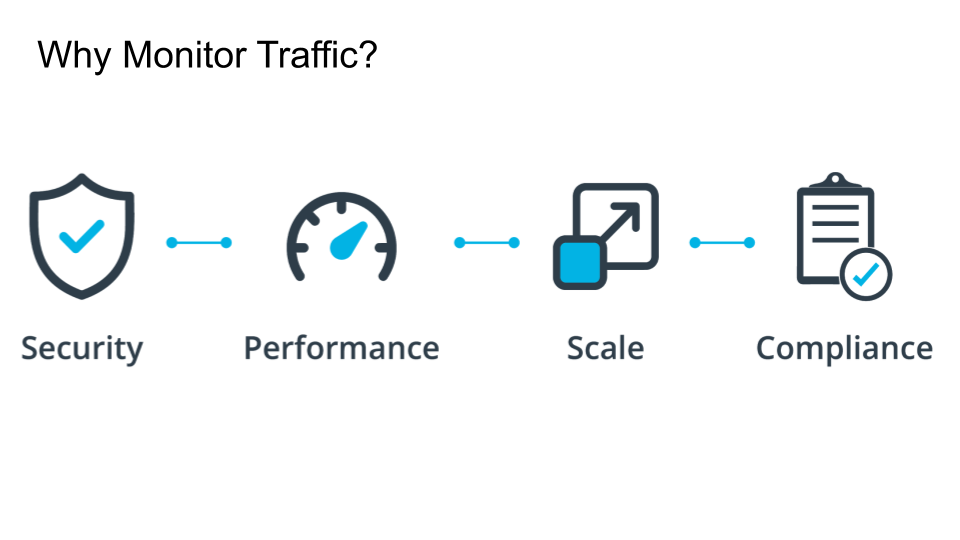
You should monitor traffic for several reasons:
Firewall logs for indications of an attack or breach.
Performance logs to catch problems before they cause an outage.
Scalability to know when to add capacity
Compliance all compliance regulations require some form of monitoring.
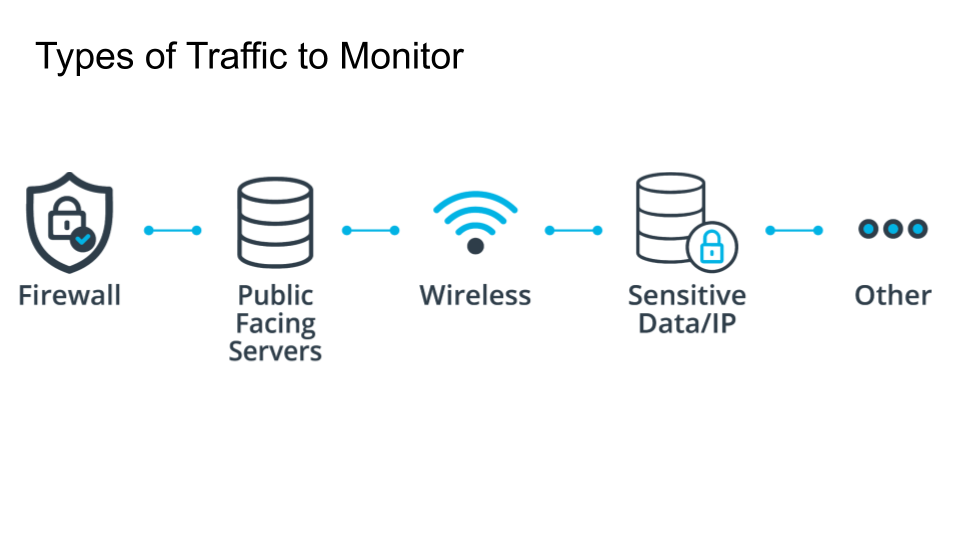
There are many types of logs you should monitor and your organization will have its own unique list. However, there are several standard items.
Firewalls As we just mentioned above, you should always monitor your firewall logs.
Public Facing Servers all traffic to and from as well as any applicable application logs.
Wireless you should monitor failed connection attempts on your wireless infrastructure.
Sensitive Data/Intellectual Property Anywhere there is sensitive information such as PII or intellectual property should be monitored.
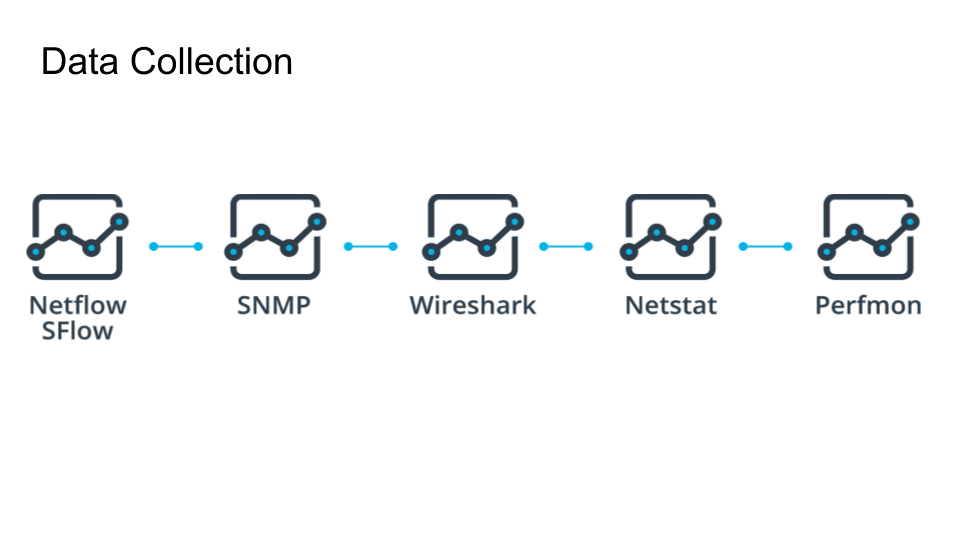
Here are several common methods for retrieving logs from networked devices:
Netflow/SFlow Netflow is a Cisco proprietary tool and SFlow is its open source counterpart. They primarily collect data from networking devices and gather information such as IPs, Ports, and protocols involved.
SNMP is Simple Network Management Protocol and it performs similarly to Netflow.
Wireshark Wireshark is an open source tool used to analyze packet captures. I'll link to more information about it below.
Netstat is a built-in utility in Windows/Mac/Linux that shows active connections to your machine. Excellent for troubleshooting.
Perfmon is a windows utility for the analysis of windows performance.
Reviewing reports generated by your security appliances/servers is a primary responsibility for analysts. Firewalls and IDS provide a wealth of information on malicious actors attempting to compromise your environment.
It is important to perform the following steps when triaging an alert report:
Research Reach out to the owner of the internal IP address and ask them if they recognize this traffic. This will help eliminate a configuration issue.
Report if the traffic is not expected, report it to the abuse contact in the WhoIs information.
Block If the traffic is from a malicious sender you can manually add it to your blocklist.
Updates ensure that any system that is being probed for a vulnerability is fully patched.
Key Terms
PII: Personally identifiable information, is any data that could potentially be used to identify a particular person. Examples include a full name, Social Security number, driver's license number, bank account number, passport number, and email address.
WhoIs: WHOIS isn't an acronym, though it may look like one. In fact, it is the system that asks the question, who is responsible for a domain name or an IP address? In other words, it's the contact information for IP addresses and Websites.
Monitoring Network Traffic Heading Image
Reasons to monitor traffic
Types of Traffic to Monitor
Data Collection Tools
Monitoring Network Traffic Further Research
Additional Resources on Data Collection Tools
Tool not covered:
ND545 C02 L03 A10 Monitoring Network Traffic Part 2
Walkthrough
ND545 C02 L03 A11 Monitoring Network Traffic Walkthrough V2